Few Screenshot di Data Breach Registry®
An intuitive Dashboard
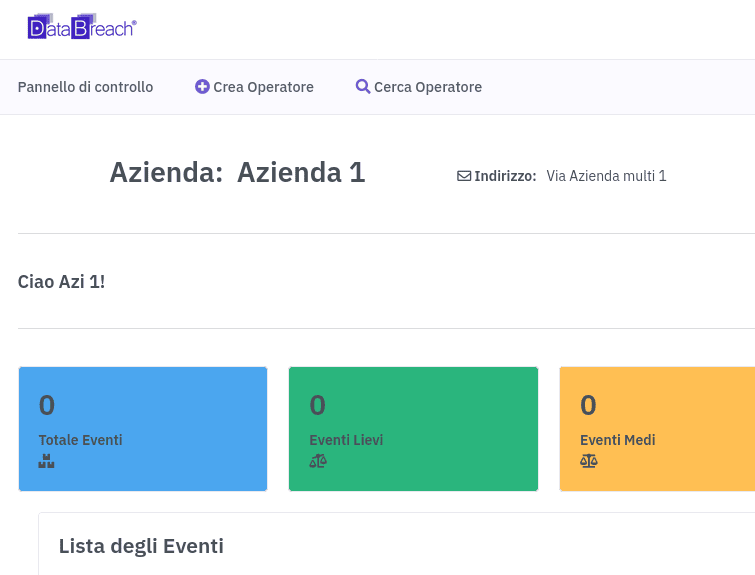
The Dashboard
Data Breach Registry® has a simple and intuitive control panel, with a simple glance the main data are at your disposal.
Strengths
Searchable event grouping
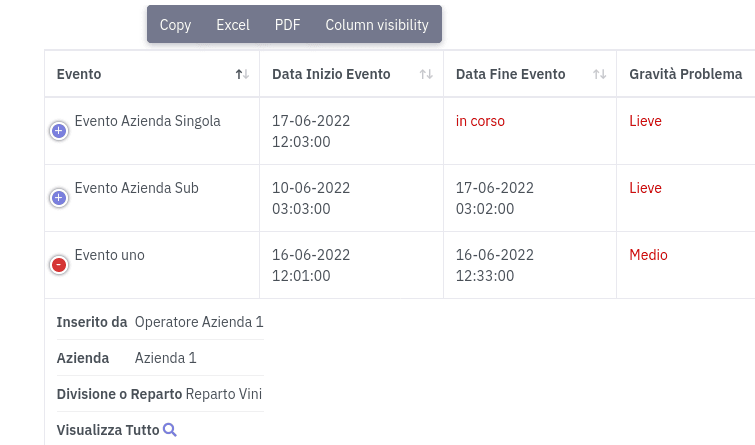
Events Search
Data Breach Registry® creates a list of Events, which is shown in a convenient grid and can be found by the internal search engine.
Strengths
PDF Generation Events
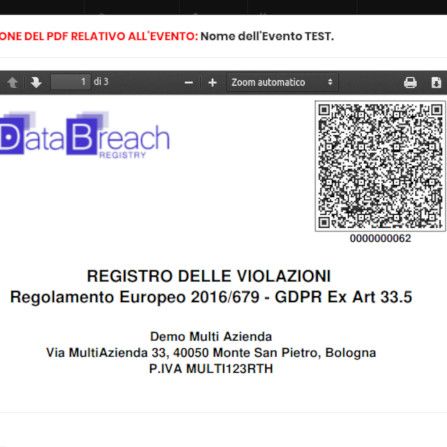
Events PDF/A Format
With Data Breach Registry®, the lists can be exported in protected PDF A, in order to guarantee the veracity of the documents.
Strengths
Event versioning
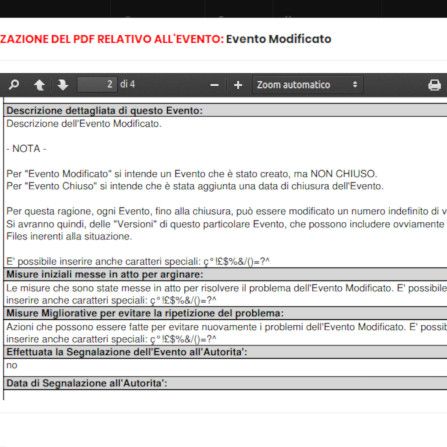
Infinite Modifications
With Data Breach Registry®, Events can be modified, whenever necessary, until they are closed. For each modification, a new and subsequent Version will be automatically generated. At the close of the Event these will no longer be editable.
Strengths
Versioning of events
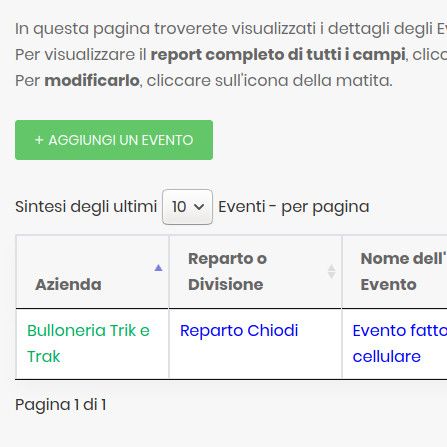
Ease to Use
Using Data Breach Registry®, compilations can be added with the push of a button, which will open the section dedicated to entering the necessary data.
Strengths
Event versioning
Design Responsive
Data Breach Registry® is fully responsive, and can be viewed and used with any device: computer, tablet or smartphone.
Strengths
DATA BREACH REGISTRY ® IS: fast according to law secure and can help you
to fulfill the obligations of the GDPR by making the
Compilation of the Register of Violations
The Register of Violations is a necessary fulfillment pursuant to the GDPR, this is clear from a careful reading of Article 33 of EU Regulation 679/2016. Here you can find the behaviors to adopt in case of having to proceed with a " Notification of a Personal Data Breach to the Supervisory Authority".
The article, in addition to listing how a notification should be made, with what methods and with what contents, specifically tells us, in point 5, that:
5. The data controller documents any Personal Data Breach, including the circumstances surrounding it, its consequences and the measures taken to remedy it. This documentation allows the supervisory authority to verify compliance with this article.
Data Breach Registry ® - DBR -was developed basing its structure both on what is reported in this specific point of the article, and taking into account the instructions of the Personal Data Guarantor Authority on how a report should be made. Keeping the Register of Violations via DBR therefore makes the Data Breach Registry ® a preparatory tool for a correct and assisted compilation of any report, as well as giving it a value high to demonstrate the Compliance of your Structure in the management of Data Breach, giving the documents generated a Legal value. The NWN Solutions Team also gives to all its Customers Support for the correct Compilation of the Infringement Register, which is included in each License.
The Features of DBR
Customer Support
Provided in both first and second level and technical support 24/7/365.
Proprietary document process
A Platform created ad HOC to Protect you Users.
Proprietary Webtool
Developed and Produced by NWN Solutions, following the Guidelines of the Guarantor.
Secure Storage
Secure archiving process, compliant with current regulations.
Uploading Attachments
Possibility to upload all the necessary Attachments within the Registry.
Download of Events in ZIP format
In order to thus allow the conservation, also in compliance with the law, of the Register.
PDF/A Generation Secured
Regulatory protection of generated files, also in English
For SMEs, Multinationals and PA
Licenses created ad HOC, for all realities.
Furthermore...
NWN Solutions Contacts
Try DBR NOW
Get started now: you can try Data Breach Registry® and its features for free for 15 days; no payment required or obligation to purchase!
Create an Account on DBR in just a few steps, dedicated to your Company's Compliance: if you have any doubts or questions, do not hesitate to contact us.The Headquarters
Business Hours
Blog
Recent posts form our Blog

Digital Omnibus e AI Act: cosa può slittare e cosa va fatto prima di agosto 2026Adriano Bertolino
 L’AI Act è già legge e alcune regole sono operative, ma la timeline dei sistemi ad alto rischio è in discussione. Il Digital Omnibus ipotizza un rinvio fino a 16 mesi, mentre EDPB ed EDPS avvertono sui rischi di deregolazione. Azioni immediate: inventario, governance integrata, design for compliance L’articolo Digital Omnibus e AI Act: cosa […]
L’AI Act è già legge e alcune regole sono operative, ma la timeline dei sistemi ad alto rischio è in discussione. Il Digital Omnibus ipotizza un rinvio fino a 16 mesi, mentre EDPB ed EDPS avvertono sui rischi di deregolazione. Azioni immediate: inventario, governance integrata, design for compliance L’articolo Digital Omnibus e AI Act: cosa […]

Scontro politico sull’AI negli Usa: la posta in giocoUmberto Bertelè
 Negli USA cresce lo scontro politico popolare contro AI e Big Tech: comunità locali contestano data center e Hollywood denuncia l’uso dei contenuti per addestrare modelli. Al tempo stesso la spinta di Trump all’AI apre fratture nel MAGA, tra antitrust, lobbying e il caso Anthropic-Pentagono L’articolo Scontro politico sull’AI negli Usa: la posta in gioco […]
Negli USA cresce lo scontro politico popolare contro AI e Big Tech: comunità locali contestano data center e Hollywood denuncia l’uso dei contenuti per addestrare modelli. Al tempo stesso la spinta di Trump all’AI apre fratture nel MAGA, tra antitrust, lobbying e il caso Anthropic-Pentagono L’articolo Scontro politico sull’AI negli Usa: la posta in gioco […]

Anthropic, OpenAI accusano di furto Deepseek: da che pulpitoGuido Scorza
 OpenAI ieri e Anthropic oggi accusano DeepSeek di distillazione e furto di proprietà intellettuale. Ma i campioni dell’AI generativa sarebbero cresciuti grazie a enormi quantità di contenuti protetti e dati personali raccolti senza licenze. Un cortocircuito che impone regole uguali e applicate a tutti L’articolo Anthropic, OpenAI accusano di furto Deepseek: da che pulpito proviene […]
OpenAI ieri e Anthropic oggi accusano DeepSeek di distillazione e furto di proprietà intellettuale. Ma i campioni dell’AI generativa sarebbero cresciuti grazie a enormi quantità di contenuti protetti e dati personali raccolti senza licenze. Un cortocircuito che impone regole uguali e applicate a tutti L’articolo Anthropic, OpenAI accusano di furto Deepseek: da che pulpito proviene […]